Karen Stephenson’s Quantum Theory of Trust
Companies can analyze, engineer, and elevate their own human networks, says the pioneering social scientist.
 |
|
Photography by Dudley Reed |
To Karen Stephenson, a maverick yet influential social network theorist, the association between trust and learning is an instrument of vast, if frequently untapped, organizational power. The act of reconnecting and talking with a trusted colleague generally triggers a resurgence of mutual memory, opening the gates to fresh learning and invention. This phenomenon, Professor Stephenson contends, is just one example of the direct cognitive connection between the amount of trust in an organization and its members’ ability to develop and deploy tacit knowledge together. Because networks of trust release so much cognitive capability, they can (and often do) have far more influence over the fortunes and failures of companies from day to day and year to year than the official hierarchy.
“People have at their very fingertips, at the tips of their brains, tremendous amounts of tacit knowledge, which are not captured in our computer systems or on paper,” says Professor Stephenson. “Trust is the utility through which this knowledge flows.”
Much has been written about the value of trust. Such social scientists as Francis Fukuyama, Mark Granovetter, and Robert Putnam have made strong cases that high-trust societies have an enormous competitive advantage over legalistic societies, in which suspicion of people is a cultural value, because the transaction costs go down. In high-trust organizations, transaction costs are similarly lower. For example, if people in two different departments or regions (say, marketing and sales, or Asia and Europe) feel enough trust to speak candidly together about their impressions of the market, the quality of work processes, and ways to improve the work, then they have many more opportunities to innovate and think together. The cost of new projects goes down accordingly. Whether high trust applies to a country or a company, the outcome is the same: More value is created when expensive, unwieldy oversight is reduced.
Professor Stephenson’s concept, which she calls the “quantum theory of trust,” explains not just how to recognize the collective cognitive capability of organizations, but how to cultivate and increase it. At age 50, Professor Stephenson is the most visible member (particularly in business circles) of a small but growing academic field called social network analysis. Originally derived from the complex math used to explain subatomic physics, it is being used to understand and manage the ineffable forces of human interaction within an organization’s walls — particularly those forces that can’t be captured in formal structures, such as pay scales and reporting relationships, but that implicitly govern the fate of every enterprise.
“The organization chart basically shows you the formal rules. But the ropes of the organization, how it actually works, is the human network,” says futurist Thornton May, one of Professor Stephenson’s former colleagues at the John E. Anderson Graduate School of Management at the University of California at Los Angeles, where she taught for most of the 1990s. “Karen, more than anyone else, knows how to make it visible.”
A trim woman, slight in stature, with large eyes set wide apart and graying hair cut straight and short, Karen Stephenson lectures at a rapid-fire pace, with twangy, slightly tongue-in-cheek forthrightness. She has not written a book to promote her work (preferring to patent her algorithms instead), and you won’t find her name on lists of top management gurus. Her academic reputation is one of contrariness; she walked away from a tenured position at UCLA because she didn’t like the direction in which the business school was moving.
Professor Stephenson came to management theory after studying the fine arts, anthropology, and chemistry; she talks about organizations as if they were still lifes, researches them as if they were tribes, and plots their decisions as if they were chemical reactions. She is simultaneously a management academic (teaching at Harvard’s School of Design and Imperial College’s School of Management at the University of London), a computer software entrepreneur (her company, NetForm International, holds the patents on a set of software algorithms for analyzing human networks), and a consultant on the nature of networks in large organizations, particularly as vehicles for change.
She helped J.P. Morgan & Company merge with the Chase Manhattan Corporation, Steelcase Inc. design a new furniture consultation service, IBM reengineer itself, and Hewlett-Packard Company foster innovation. Since the events of September 11, 2001, she has also become a military researcher. Under the auspices of a new government contracting firm, she is helping the U.S. Defense Advanced Research Projects Agency’s Information Awareness Office (the counterterrorism branch of the same government research agency that created the original design of the Internet) draw inferences about the weak links in Al Qaeda’s network.
In all these assignments, her research documents what savvy managers have always known intuitively: The form and substance of talk in an organization is as palpably influential on performance as a magnetic field is on a cluster of iron filings. Companies, she says, can exert far greater control over their competitiveness and their future than most researchers have ever thought possible, by putting the right people in the right places and fostering new opportunities for them to talk with each other.
Anatomy of a Network
To understand Professor Stephenson’s work, start with the conventional image of an organization: the hierarchy, as represented by any formal organization chart. Then imagine laying over it diagrams of various other kinds showing human networks that are influential within the organization. One overlay might depict day-to-day assignment contacts, which Professor Stephenson calls the “work network.” Another diagram might show the social network — people who spend time together outside work. A third might show whom people turn to for career guidance (the career advice network).
Like the transparencies in a medical textbook, organizational network diagrams all reveal different circulatory systems, but instead of showing the flow of blood, they depict the circulation of information. The data charted in these diagrams could be gathered in various ways (direct observation, tracking e-mails, reading minutes of meetings), but, in practice, network researchers tend to rely on surveys. Karen Stephenson requires at least 80 percent of the people in organizations she analyzes to fill out confidential questionnaires that ask them to name those they work with personally, those they turn to for career advice, those they look to for new ideas or creative collaboration, and those with whom they socialize.
The results can help explain even the most puzzling successes and failures. Consider one case Professor Stephenson researched: the flawed CEO succession in a new R&D subsidiary of a major telecommunications company, which harmed the company’s profitability. The story, based on surveys Professor Stephenson conducted, is revealed in Exhibits 1 through 3.
These diagrams show the connections for four key people: the CEO, then nearing retirement, and three of his direct reports, Joe, Diane, and Stan. Those three, like most senior executives, were richly connected to others at the company, but the qualities of their connections were different. Diane, for example, was critical to the day-to-day work of the enterprise. Exhibit 1, the diagram of the work network, shows it: Among the 15 other people included in this chart, seven worked with Diane every day. She was exceptionally plugged in because of her superior knowledge of the company’s key technologies.
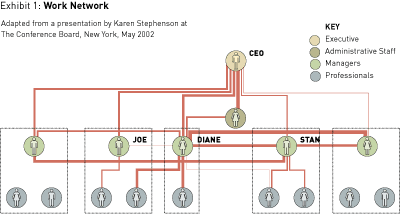
Professor Stephenson, in fact, refers to Diane as a “hub” in the work network: an individual so well connected to others that she plays an indispensable role in keeping the flow of information going. Hubs are characterized, Professor Stephenson says, by an extraordinarily high level of trust: People know what to expect from them. Their calls are returned. They attend all the key meetings. They convey news. Those who worked closely with Diane, for instance, hardly needed to speak to each other directly; she became their main communication channel.
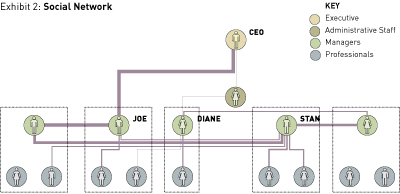
But Diane’s social links (Exhibit 2) and her career advice network (Exhibit 3) are minimal. She was, in short, a workaholic whom everyone depended on but nobody felt close to. “She was sick of her work colleagues,” says Professor Stephenson, “and just wanted to go home at night and veg out.”
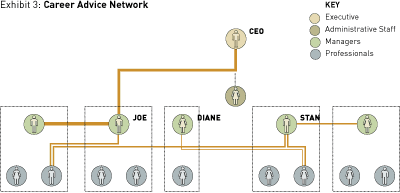
Diane also was a time bomb. She wanted desperately to be promoted to a higher position, believed she deserved it, and felt almost disenchanted enough to leave the company. “Remember, knowledge in this company was generated through mutual trust and exchange,” says Professor Stephenson. “If Diane, God forbid, died in a plane crash, a lot of that company’s capability would be gone.”
Diane’s polar opposite was Joe, another of the CEO’s direct reports. In Exhibit 1, there is only one thin link between Joe and Diane, representing the minimum collaboration that they absolutely could not avoid. “These two executives actually did not see eye to eye,” says Professor Stephenson.
Joe, as it happens, was not very knowledgeable about the company’s technology or business, nor did he get much trust or respect from others in the organization. But he had one enormous asset: a strong social bond with the CEO, represented by the thick line in Exhibit 2. Joe and the CEO regularly played golf, and afterward, on the “19th hole,” as Professor Stephenson puts it, they plotted the future of the company. For this CEO, socializing outside work with Joe had come to substitute for all other meaningful learning contacts. That, in turn, had weakened the organization and made it far more difficult for him to choose a successor. Because all of this was taking place in a turbulent and highly competitive business environment with an overloaded staff, nobody thought to speak out about the lack of balance in the CEO’s network.
Then the CEO retired and passed the mantle to Joe. Diane left the firm. Joe tried to use his connections with others as a surrogate for the knowledge he lacked — and whether intentionally or not, they made it difficult for him to do so. Joe was quickly dismissed by the board, after three months of terrible performance that could have permanently crippled the company. “Someone like Joe, who is neither knowledgeable in himself nor connected within a network of trust, is at high risk of being undermined by others or failing,” says Professor Stephenson.
As it happened, however, with Diane and Joe out of the picture, there was now room for a third individual, Stan, to step into the CEO’s position. Stan’s work connection with the CEO had been fairly weak, and he was only moderately well-connected in the social network. However, Stan was strong in the career network; he met regularly with three other people to make sense of the organization and its future direction and to plot its common course. This was enough to give other people throughout the organization a sense that they could rely on Stan, and that was enough for the board to recognize his value and appoint him CEO. Stan had always kept himself in the background, but he turned out to be very competent. In the next few years, the division recouped much of its performance and profitability, although it never regained the growth momentum that was squandered when Diane left.
The effectiveness and power of an individual, in short, depends not just on his or her position in the hierarchy, but on the person’s place in a variety of intertwined networks.
If you were to plug all the data from Professor Stephenson’s questionnaires into network modeling software (as she does), you would end up with a series of maps much more complex than the ones shown in Exhibits 1 through 3, showing a large number of possible networks. Professor Stephenson tends to focus on six networks: the three described in this anecdote, plus networks of innovators, established experts, and process improvers. (See the “Six Varieties of Knowledge Networks,” at the end of this article.) A typical social network analysis uncovers and tracks the number of links among individuals in any of these networks, the frequency with which people communicate, the relative significance of their communication, and the number of people through which a message passes. Looking at these maps of informal networks, you start to see, as Professor Stephenson puts it, “how the network itself has an intelligence, more than the sum of its parts and beyond the cognition of any one individual.”
You also see how to intervene far more effectively. Although the telecommunications company weathered its divisional succession crisis, a preliminary network analysis would have exposed hidden staff problems and opportunities. It would have shown how overburdened Diane was, and it would have helped a savvy leader cultivate her far more effectively — by reorienting her job and setting aside time for her to codify her knowledge or impart it to others. It would have identified Stan as a quiet but highly significant potential leader, so he could have been made part of the management team earlier. It would have made clear the extent to which Joe needed leadership development. It also would have identified up-and-comers lower in the hierarchy. Perhaps most important, an analysis would have given someone (a trusted head of human resources, perhaps) the ability to approach the CEO and say, “There’s a lot going on that you are not aware of, and it’s affecting your capability and that of the entire division.”
Double-Helix Management
Professor Stephenson doesn’t suggest replacing hierarchies with networks. Rather, she sees organizations as a sort of double-helix system, with hierarchy and networks perpetually influencing each other, ideally co-evolving over time to become more effective.
But if a CEO wants to strengthen a hierarchy, he or she can also use networks to do so, by establishing new relationships based on three kinds of network “nodes” — categories of people whose personalities and patterns of relationships crop up again and again in the software analyses. The first of these is the hub, the kind of person who becomes a gathering and sharing point for critical information. Hubs show up on network maps like the centers of star clusters, sometimes with dozens of links radiating out from them. Diane, the frustrated subordinate in the CEO succession story, was a key hub because she had what Professor Stephenson calls “centrality”: She ranked high as a connector among people; the shortest route to the information needed about work assignments was often through Diane.
Stan, the executive who eventually became CEO, was a different kind of network archetype, a “pulsetaker.” Pulsetakers, says Professor Stephenson, carefully cultivate relationships that allow them to monitor the ongoing health and direction of the organization. It’s not always easy to tell who the pulsetakers are.
“Even I, after 30 years of research, can’t see them by staring at the diagrams,” she says. “You can only detect them through the mathematics” — by which she means the algorithmic analysis of survey data. A pulsetaker’s patterns of connection show a distinct mathematical pattern, with links that are relatively sparse, but frequently used and diverse. Every now and then someone gets colloquially recognized as the first to sense changes in the wind, and to intervene in subtle but powerful ways. Professor Stephenson likens them to “prairie dogs, poking their heads above the cubicle tops to see what’s going on.” They make good CEOs in times of crisis, Professor Stephenson says.
The third key type of individual is the “gatekeeper.” Gatekeepers are information bottlenecks, controlling the flow of contact to a particular part of the organization, thus making themselves indispensable. In many manufacturing companies, managers of key assembly plants are well known as gatekeepers, protecting the plant’s integrity (and their own position) by keeping a tight rein on the information flowing in either direction between the plant and the rest of the company.
Although hubs, pulsetakers, and gatekeepers are Professor Stephenson’s terminology, the ideas are not unique. The hub concept is a long-standing artifact of social network research, and gatekeepers were first identified by Massachusetts Institute of Technology professor Thomas J. Allen, Jr. Professor Stephenson, however, has taken the research beyond description and into prescription, suggesting ways to intervene and improve the organization, literally by putting people into different roles based on their capacities as networkers.
“If I wanted to increase learning in a company,” she says, “I would take a gatekeeper in an innovation network and put him or her with a pulsetaker in an expert network. That’s an algorithm for facilitating the distribution of knowledge.”
Professor Stephenson’s work has come to seem less counterintuitive in the last year or two, especially as an organization like Al Qaeda has demonstrated how powerful informal connections can be.
Then there is the growing awareness that ideas and trends, like epidemics, spread in nonlinear fashion, with the makeup of human contact being the most important factor. New Yorker writer Malcolm Gladwell described this concept in his bestseller The Tipping Point: How Little Things Can Make a Big Difference (Little, Brown & Company, 2000). He was later introduced to Professor Stephenson at a dinner party convened by a Saatchi & Saatchi executive — someone who was a “hub” in Professor Stephenson’s terms, or a “connector” in Mr. Gladwell’s — who knew them both. He immediately recognized her as not just a kindred spirit, but someone who had applied research rigor to the phenomenon that he had popularized.
“My whole thesis is that certain people play critical networking roles,” says Mr. Gladwell. “Karen can actually go to a company and point them out. And yet her work is quite subversive in a certain way. It’s hard to accept the idea that there are people who play critical roles who don’t show up on the organization chart. I’ve never heard anyone say, ‘This person is a powerful networker, and deserves a raise.’ But Karen gives us a tool for measuring the contribution of these social types.”
Analyzing Interdependence
Social network theory evolved from studies outside corporations — for instance, of indigenous communities in New Guinea adopting new ideas, or of the spread of HIV through sexual contact. The field is based on the idea that the modeling techniques theoretical physicists use to study subatomic particles can be applied to build elaborate computer simulations of something equally complex: the patterns of contact and colloquy among human beings. (For more on the mathematics behind social network theory, see “Network Theory’s New Math,” click here.)
The conclusions that network researchers reach have a way of illuminating the otherwise unexplainable mysteries of organizational triumphs and disasters. Traditional system analysis methods such as econometrics “assume that everybody acts independently,” says Carnegie Mellon University professor David Krackhardt, editor of the Journal of Social Structure, one of the field’s leading scholarly publications. “Network analysis,” he adds, “does just the opposite. It assumes that everyone is interdependent. It provides a kind of pattern recognition that makes sense of the complex relationships among people: Here are the bottlenecks; here are the points that are essential to a system, so that if you remove that node, the network falls apart.”
Maria Leo, a senior human resources executive at Merrill Lynch & Company during the late 1990s, who commissioned Professor Stephenson for a study of the company’s human resources function, calls social network analysis “a high-level MRI of the organization.
“From that, you’re able to dig down deeply and use the data to have an effect on people,” she says. At Merrill Lynch, she discovered that the most effective recruitment managers were hubs: They stayed in close contact with most of their field personnel, and this led directly to a higher “hit ratio,” the proportion of interviews that led to actual hires. She conducted one-on-one counseling sessions with other human resources managers, showing them how more hublike behavior could benefit their departments.
Professor Stephenson also works regularly with a half-dozen architecture and design firms, including the pioneering office furniture manufacturer Steelcase. Partly on the basis of her network theories, Steelcase established a practice called community-based planning. When embarking on an office design for a client, Steelcase conducts a Stephenson-style network analysis of the communication flows, along with a more conventional videocamera analysis of the current workspace ambiance. The designers then reveal the results to the employees who will be working in the new office environment, and invite everyone to design the new setting together. One of the first testing grounds of this approach was an NCR Corporation design facility in Dundee, Scotland; the employees gathered around giant diagrams of “work networks” and “decision-making networks” projected on wall-sized whiteboards to figure out who would need to be located near whom to promote casual contact.
“There are multiple factors influencing how you might lay out a floor,” says Jim Prendergast, a principal with Perkins and Will, an international workplace design firm with which Professor Stephenson works regularly. “They include the geometry of the building, the functions of the hierarchy, the rhythms of door openings, and the axis of circulation. But all of those are essentially abstractions. Karen’s work reminds us of the key human relationships that can get stretched, or even destroyed, if the design is based only on these abstractions.”
Molecular Studies
The design initiatives, plus a fair amount of business press, have made Professor Stephenson prominent among social network researchers, but she is far from a hub in either management or academic circles. She rarely goes to conferences and doesn’t take part in many research colloquies. Although she teaches at three schools (Harvard, the University of London, and the Stevens Institute of Technology in Hoboken, New Jersey), her primary office is a three-room suite in a warren of creative studios above the Strand bookstore in Greenwich Village, New York.
Professor Stephenson’s interest in social networks dates to her undergraduate years majoring in art and chemistry at Austin College in Texas, where she discovered that she had a predilection for pattern recognition. In art history classes, she could recognize not just the artist of a work, but the date, by reading the characteristics of the brush strokes. She began selling her own paintings to New York galleries, then grew disillusioned with art and moved to the University of Utah to study quantum chemistry.
But instead of submolecular particles, she became interested in people. While managing the 200-person chemistry lab, she began to notice that the kinds of radioactive degradation she saw in macromolecular chemistry were not that different from the patterns of communication breakdowns and rivalry that she saw in the lab. “There was more to calculus than devising formulas for describing the shape of space,” she says. “There was also a calculus of human exchange.” This led her to an interest in the archaeological record of ancient trading patterns, the oldest available data about the roots of human exchange. And that, in turn, led her to a shift of academic field, to anthropology; she began to conduct field archaeology research in the Middle East. A paper she wrote about algorithms for analyzing trade networks caught the eye of Carl Lamberg-Karlovsky, director of the Peabody Museum, who introduced her to Harvard’s anthropology department, which accepted her as a Ph.D. candidate. Working part-time in labs and then technology businesses to support her studies, she began to see today’s organizations as modern-day equivalents to the trade networks of ancient times.
In her doctoral dissertation on the technology company Bolt, Beranek and Newman (BBN), Professor Stephenson (with Harvard statistical scientist Marvin Zelen) devised a formula for ranking the significance of individuals as knowledge conduits. Information scientists at BBN, which was founded by MIT professors as an acoustic-design company, had invented (among other things) the packet-switching technology underlying the Internet and had chosen the @ symbol for use in e-mail addresses. Interestingly, researchers at the Harvard Business School had been trying, unsuccessfully, to get permission to conduct a case study on this highly innovative company for 25 years. Ms. Stephenson, however, was the first prospective researcher from the school of anthropology. It turned out that BBN cofounder Richard Bolt, who was still active in the firm, had been close friends with Margaret Mead. In Ms. Stephenson’s interview with him, he said, “Well, if anyone can understand us, an anthropologist should.” She began to use the formula from her dissertation to calculate how networks changed over time, working initially at Harvard, then as a UCLA faculty member, and currently from her offices in New York.
Trust and Transactions
For all of Professor Stephenson’s observations about the value of trust, there’s a cloak-and-dagger quality to her demeanor, particularly when she is figuring out whether to take on an assignment. She seems to alternate between open enthusiasm and suspicion; it’s as if her own theories have sensitized her to the flip side of trust: betrayal. But once she is fully committed, she digs deep into the heart of the organization, conducting analyses over the course of a year or two. Because she must interview or survey so many people to do an analysis, she claims to have the largest data bank of business network survey results in the world.
Often, Professor Stephenson enters a company through the human resources department to research what is seen as a personnel problem. She came to Merrill Lynch to help explore why some human resources managers were more effective than others. But inevitably, she touches on strategic issues, because the organization’s ability to implement any new strategy depends primarily on the way knowledge courses through its networks. If the CEO is a hub, that makes a difference; if a gatekeeper dominates a particular strategic product or region, that makes another kind of difference. And if the relationships between top executives and others are devoid of trust, or if key sources of information in the informal networks are not formally recognized or rewarded, that can paralyze an organization.
“All along, I’ve been implicitly studying trust,” says Professor Stephenson. “But I only came to a full realization of it in the last couple of years.”
Professor Stephenson’s quantum theory of trust holds great potential as a diagnostic method for the unquantifiable aspects of business. Imagine that at any given moment, you could analyze the health of an organization’s networks. For instance, a company might have a healthy work network (with a great deal of open information flow about processes and very little workaholism), a medium-grade social network (with little real contact but also little pressure), and a low-quality network for what Professor Stephenson calls “continuous improvement” — the ability to innovate new processes easily. Any organization can be stunted in one of these areas and bountiful in another.
Professor Stephenson suggests that most organizations do not remain static. Their network health profiles continually change. An organization’s path from one network health profile to another not only is predictable, she says, it can be influenced. There are archetypal patterns that repeat, over and over, and, depending on the prevalent pattern, make it possible for one company to thrive where another fails. A startup technology company might begin with a low work/high social/medium improvement profile, as people first get to know each other. Then, as venture capital and deadlines kick in, the profile would move to high social/high work/medium improvement. And then there might be a betrayal by one of the senior executives. At this moment, the fate of the company’s networks hangs in the balance. Does its improvement capability, for instance, go up or down? Does its social capability flatten to the point where people leave the company? Or can the strength of the networks, fortified by the trust people feel for one another, override the crisis?
Part of Professor Stephenson’s current research is devoted to tracking the patterns of movement from one network profile to another, patterns that recur from organization to organization. “It’s like a Rubik’s cube,” she says, “turning in three dimensions, with the organization spiraling through the various quadrants in a helixlike motion over time.” She is also articulating the factors that make the most difference in moving the networks in healthier directions — factors in which trust is always central. For example, one easy way to improve the level of trust, anytime and anywhere, is simply to increase the speed with which people respond to communication. When people return our calls or e-mails quickly, it sends a signal that we can rely on them because our connection, however distant, is important enough to claim some of their attention. “Human beings always keep an internal accounting system of who owes what to whom,” says Steve Haeckel, director of strategic studies at IBM’s Advanced Business Institute, who has collaborated with Professor Stephenson for 10 years on some of the trust-related research she’s done. “Response time is one indicator of the degree of trustworthiness of the other individual.”
You can also weaken trust in networks by removing key people. This approach to altering networks takes on particular relevance in Professor Stephenson’s current work with the Defense Department’s research agency. She is working with the agency to identify key nodes of Al Qaeda and other terrorist networks; undermining trust within those networks may be as effective a form of defense against them as, say, attacking their remaining strongholds with military force.
It may seem unnerving to think of networks as something that can be undermined or manipulated; after all, they are composed of human friendship and behavior. But politicians and leaders (as well as novelists and dramatists) have long known, if only intuitively, how a mere word of betrayal or trust, or the movement of a particular key person from one spot to another, can significantly change an outcome. Professor Stephenson’s theories, if they turn out to be correct, will simply provide a scientific underpinning for this awareness — and a far more powerful and reliable capability, for those who choose to use it.
And there lies the rub for the rest of us. Do we want to live in a world where people, even those with the best of intentions, have this kind of power to disrupt and reshape networks? Or perhaps we already live in such a world, and it’s up to us to engender the kind of trust that will, in the end, make it palatable to remain there. ![]()
Reprint No. 02406
|
Six Varieties of Knowledge Networks |
|
In any culture, says Karen Stephenson, there are at least six core layers of knowledge, each with its own informal network of people exchanging conversation. Everybody moves in all the networks, but different people play different roles in each; a hub in one may be a gatekeeper in another. The questions listed here are not the precise questions used in surveys. These vary on the basis of the needs of each workplace and other research considerations (“Don’t try this at home,” says Professor Stephenson), but they show the basic building blocks of an organization’s cultural makeup. 1. The Work Network. (With whom do you exchange information as part of your daily work routines?) The everyday contacts of routinized operations represent the habitual, mundane “resting pulse” of a culture. “The functions and dysfunctions; the favors and flaws always become evident here,” says Professor Stephenson. 2. The Social Network. (With whom do you “check in,” inside and outside the office, to find out what is going on?) This is important primarily as an indicator of the trust within a culture. Healthy organizations are those whose numbers fall within a normative range, with enough social “tensile strength” to withstand stress and uncertainty, but not so much that they are overdemanding of people’s personal time and invested social capital. 3. The Innovation Network. (With whom do you collaborate or kick around new ideas?) There is a guilelessness and childlike wonderment to conversations conducted in this network, as people talk openly about their perceptions, ideas, and experiments. For instance, “Why do we use four separate assembly lines where three would do?” Or, “Hey, let’s try it and see what happens!” Key people in this network take a dim view of tradition and may clash with the keepers of corporate lore and expertise, dismissing them as relics. 4. The Expert Knowledge Network. (To whom do you turn for expertise or advice?) Organizations have core networks whose key members hold the critical and established, yet tacit, knowledge of the enterprise. Like the Coca-Cola formula, this kind of knowledge is frequently kept secret. Key people in this network are often threatened by innovation; they’re likely to clash with innovators and think of them as “undisciplined.” 5. The Career Guidance or Strategic Network. (Whom do you go to for advice about the future?) If people tend to rely on others in the same company for mentoring and career guidance, then that in itself indicates a high level of trust. This network often directly influences corporate strategy; decisions about careers and strategic moves, after all, are both focused on the future. 6. The Learning Network. (Whom do you work with to improve existing processes or methods?) Key people in this network may end up as bridges between hubs in the expert and innovation networks, translating between the old guard and the new. Since most people are afraid of genuine change, this network tends to lie dormant until the change awakens a renewed sense of trust. “It takes a tough kind of love,” says Professor Stephenson, “to entrust people to tell you what they know about your established habits, rules, and practices.” |
| Authors
Art Kleiner, art@well.com is the “Culture & Change” columnist and a regular contributor of “The Creative Mind” profiles for strategy+business. He teaches at New York University’s Interactive Telecommunications Program. His Web site is www.well.com/user/art. Mr. Kleiner is the author of The Age of Heretics (Doubleday, 1996); his next book, Who Really Matters: The Core Group Theory of Power, Privilege, and Business Success, will be published by Doubleday Currency in August 2003.
|